Refined cyber actors backed by Iran known as OilRig have been linked to a spear-phishing advertising and marketing marketing campaign that infects victims with a model new strain of malware known as Menorah.
“The malware was designed for cyberespionage, capable of determining the machine, learning and importing data from the machine, and downloading one different file or malware,” Sample Micro researchers Mohamed Fahmy and Mahmoud Zohdy said in a Friday report.
The victimology of the assaults simply isn’t immediately acknowledged, although the utilization of decoys signifies not lower than considered one of many targets is an organization located in Saudi Arabia.
Moreover tracked beneath the names APT34, Cobalt Gypsy, Hazel Sandstorm, and Helix Kitten, OilRig is an Iranian superior persistent danger (APT) group that focuses on covert intelligence gathering operations to infiltrate and maintain entry inside targeted networks.
The revelation builds on recent findings from NSFOCUS, which uncovered an OilRig phishing assault ensuing throughout the deployment of a model new variant of SideTwist malware, indicating that it’s beneath regular development.
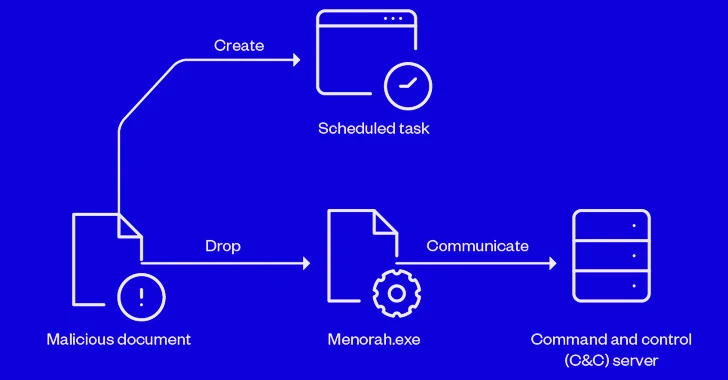
Inside the latest an an infection chain documented by Sample Micro, the lure doc is used to create a scheduled job for persistence and drop an executable (“Menorah.exe”) that, for its half, establishes contact with a distant server to await extra instructions. The command-and-control server is at current inactive.
Fight AI with AI — Battling Cyber Threats with Next-Gen AI Tools
Capable of take care of new AI-driven cybersecurity challenges? Be a part of our insightful webinar with Zscaler to deal with the rising danger of generative AI in cybersecurity.
The .NET malware, an improved mannequin of the distinctive C-based SideTwist implant discovered by Check Degree in 2021, is armed with various choices to fingerprint the targeted host, document directories and knowledge, add chosen data from the compromised system, execute shell directions, and acquire data to the system.
“The group persistently develops and enhances devices, aiming to reduce security choices and researchers’ detection,” the researchers talked about.
“Typical of APT groups, APT34 demonstrates their large property and numerous skills, and might seemingly persist in customizing routines and social engineering methods to utilize per targeted group to ensure success in intrusions, stealth, and cyber espionage.”
Thank you for being a valued member of the Nirantara family! We appreciate your continued support and trust in our apps.
-
Nirantara Social - Stay connected with friends and loved ones. Download now:
Nirantara Social

-
Nirantara News - Get the latest news and updates on the go. Install the Nirantara News app:
Nirantara News

-
Nirantara Fashion - Discover the latest fashion trends and styles. Get the Nirantara Fashion app:
Nirantara Fashion

-
Nirantara TechBuzz - Stay up-to-date with the latest technology trends and news. Install the Nirantara TechBuzz app:
Nirantara Fashion

-
InfiniteTravelDeals24 - Find incredible travel deals and discounts. Install the InfiniteTravelDeals24 app:
InfiniteTravelDeals24

If you haven't already, we encourage you to download and experience these fantastic apps. Stay connected, informed, stylish, and explore amazing travel offers with the Nirantara family!
Source link